LetsDefend level 1 alert SOC127 - SQL Injection Detected event-id 60
Details
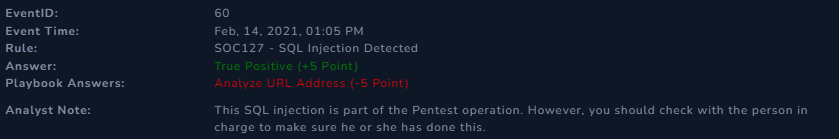
EventID: 60
Event Time: Feb. 14, 2021, 1:05 p.m.
Rule: SOC127 - SQL Injection Detected
Level: Security Analyst
Source Address 172.16.20.5
Source Hostname PentestMachine
Destination Address 172.16.20.4
Destination Hostname gitServer
Username kali
Request URL https[:]//172.16.20.4/?id=1 and (1,2,3,4) = (SELECT * from db.users UNION SELECT 1,2,3,4 LIMIT 1)
User Agent Penetration Test - Do not Contain
Device Action Allowed
playbook
Collection Data
- Source Address
172.16.20.5(PentestMachine) - Destination Address
172.16.20.4(gitServer) - User-Agent
Penetration Test - Do not Contain
おそらくペンテスト中の操作がアラートとなった。
Search Log
search from 172.16.20.5 to 172.16.20.4
| # | DATE | TYPE | SOURCE ADDRESS | SOURCE PORT | DESTINATION ADDRESS | DESTINATION PORT |
|---|---|---|---|---|---|---|
| 356 | Feb, 14, 2021, 01:01 PM | Firewall | 172.16.20.5 | 45873 | 172.16.20.4 | 443 |
| 410 | Jun, 13, 2021, 04:23 PM | Firewall | 172.16.20.5 | 53222 | 172.16.20.4 | 22 |
356
Request URL: https[:]//172.16.20.4/?id=1 and (1,2,3,4) = (SELECT * from db.users UNION SELECT 1,2,3,4 LIMIT 1) Request Method: GET Device Action: Allowed
このSQL Injectionが通ったなら超甘々なvalidationですね。
410
No Log
Analyze URL Address
一応Pentestマシンからのアクセスなので、
Answer: Non-malicious
Add Artifacts
| Value | Type | Comment |
|---|---|---|
| 172.16.20.5 | IP Address | PentestMachine |
| https[:]//172.16.20.4/?id=1 and (1,2,3,4) = (SELECT * from db.users UNION SELECT 1,2,3,4 LIMIT 1) | URL Address | SQL Injection (Pentest |
End
似たようなことを前にもやってマイナスポイントだった気がするが、SQL Injection自体はMaliciousだからMaliciousであるか。